Continuous Attack Surface Discovery
Horusion™ provides continuous external visibility through an outside-in security approach, mapping an organization’s entire digital footprint from an attacker’s perspective. The platform autonomously discovers internet-facing assets, identifies vulnerabilities, and provides AI-driven remediation insights.
One Platform.
Complete Attack Surface Intelligence.
Managing your evolving attack surface should not require multiple tools. Horusion™ brings everything together in a single platform. Just enter your organization's name, and Horusion™ does the rest. No additional seed information such as domains, IP addresses, or customer data is required.
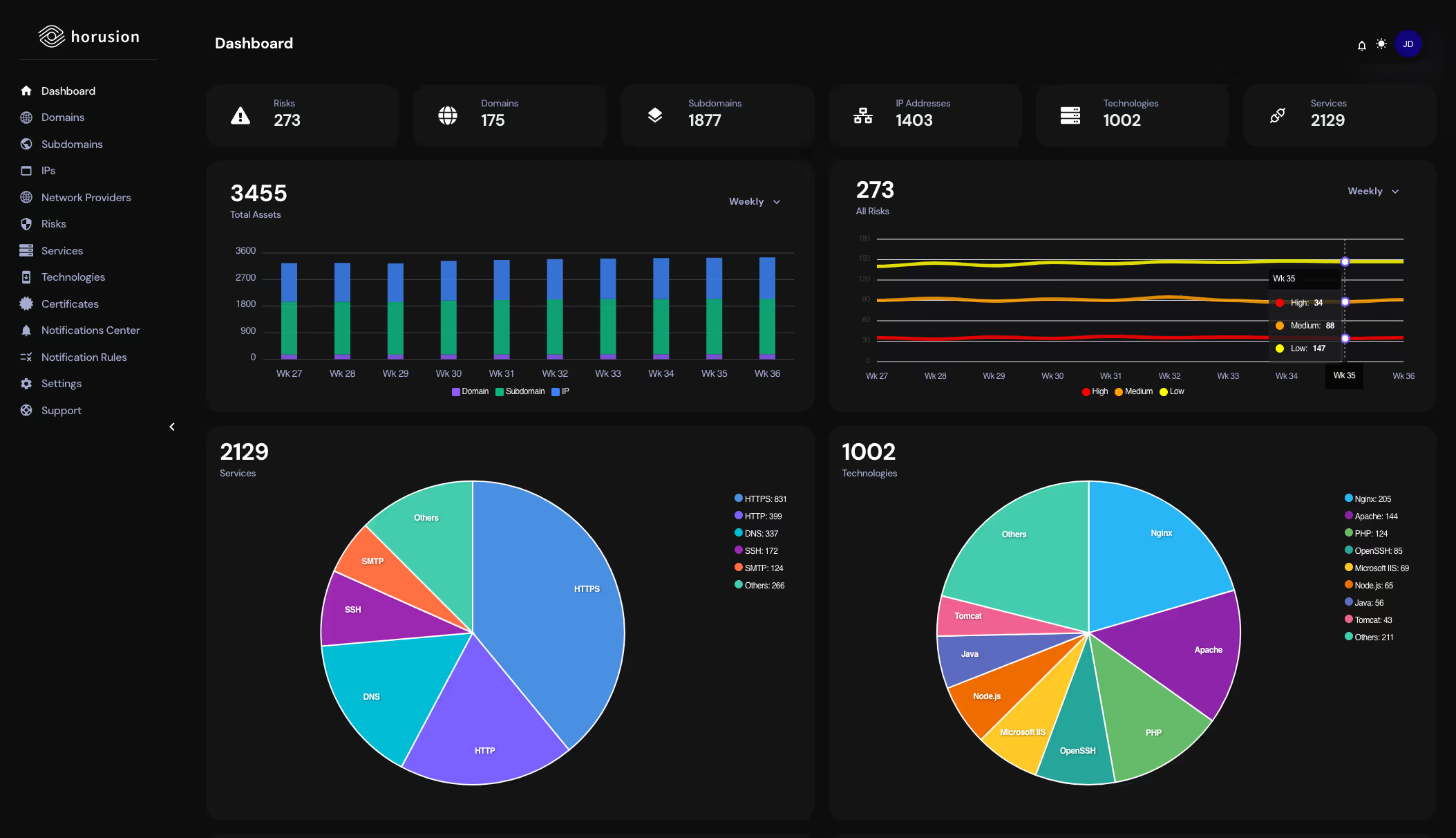
Continuous Attack Surface Discovery
Automatically discovers all internet-facing assets, including domains, subdomains, IPs, SSL/TLS certificates, technologies, and services. Maintains a continuously updated map of the organization’s exposed digital footprint.
Automated Risk Identification
Detects misconfigurations, open ports and services, expired certificates, subdomain takeover risks, known vulnerabilities (CVEs), and exposed administrative interfaces, then prioritizes risks from critical to low.
Actionable Security Insights
Provides AI-driven remediation guidance that helps security teams respond faster, reduce manual investigation, and maintain consistent, high-quality security actions across all detected risks.
Active Scanning (Selected Assets)
Performs targeted, on-demand active scans on selected assets to identify deeper technical weaknesses similar to those uncovered during penetration tests.
Rule-Based Notifications & Alerts
Provides configurable email and SMS notifications, letting customers choose when and for which events to receive alerts such as new risks, discovered assets, or expired SSL certificates.
Seamless Integrations & Reporting
Integrates with customers’ internal systems such as ServiceNow or SSO to streamline workflows within existing security operations. Generates reports in CSV, Excel, or PDF formats.
Practical Use Cases That Drive Results
These real-world use cases show how Horusion™ turns visibility into action.
Certificate Expiration Monitoring
Avoid security gaps by tracking and managing SSL/TLS certificates before they expire.
Outdated Software & Vulnerability Filtering
Instantly identify software versions with known vulnerabilities, like Log4j, and filter affected assets.
Tagging OT Assets for Better Organization
Easily categorize operational technology (OT) assets to ensure clear separation from IT resources.
Geographic Heatmap View
Pinpoint asset distribution across global infrastructure.

Subsidiaries & M&A Monitoring
Extends discovery and monitoring across subsidiaries and acquisitions, providing clear outside-in visibility into the risks introduced through corporate structure changes. Identifies hidden assets and inherited exposures, supports due diligence before, during, and after deals, and continuously monitors newly acquired entities to help keep an expanding organization secure. Third-party coverage (suppliers and vendors) is available on request and requires an NDA and written authorization.
Stay Compliant & Secure
Compliance requires full visibility across all internet-facing assets and risks. Horusion™ maintains an always up-to-date inventory as domains, IPs, and cloud services change, providing continuous tracking and clear reporting to support audit readiness and compliance requirements.

All Features. One Plan.
Built to Scale.
Horusion™ is built to take the complexity out of pricing. Full access is available from day one: no feature tiers, no guesswork. Instead of picking and choosing what might be needed, everything is included. Each plan simply scales with the number of assets being monitored.
